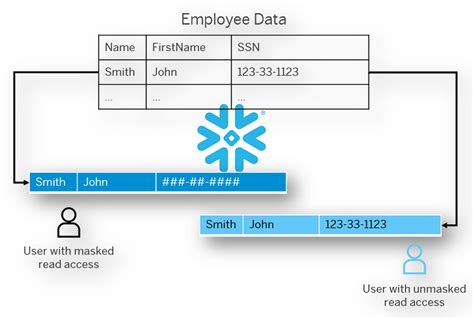
Masking data is a critical process in data protection and privacy, allowing organizations to conceal sensitive information while still utilizing the data for various purposes such as testing, development, and analysis. This technique is especially important in industries that handle sensitive information, such as healthcare, finance, and government. In this article, we will delve into the concept of data masking, its importance, and explore five ways to mask data effectively.
Key Points
- Data masking is a method used to protect sensitive data by replacing it with fictional but realistic data.
- It is crucial for compliance with data protection regulations and for securing sensitive information.
- Static data masking involves permanently masking data in a database or file.
- Dynamic data masking hides data in real-time, without altering the original data.
- On-the-fly data masking is a method that masks data as it is being moved or processed.
Understanding Data Masking
Data masking is essentially about creating a version of your data that is not sensitive, making it safe for use in environments where sensitive data is not needed or could pose a risk. This can include development, testing, and even training environments where real data might not be necessary but the structure and format of the data are crucial for accurate simulations or analyses. The goal is to protect personally identifiable information (PII), financial information, and other sensitive data types from unauthorized access or breaches.
Types of Data Masking
There are several types of data masking techniques, each serving different purposes and offering varying levels of protection and flexibility. These include static data masking, dynamic data masking, and on-the-fly data masking, among others. Static data masking involves permanently masking data in a database or file, creating a masked copy of the data that can be used in non-production environments. Dynamic data masking, on the other hand, hides data in real-time, without altering the original data, making it particularly useful for applications where data needs to be protected based on user roles or other dynamic conditions.
5 Ways to Mask Data

Data masking can be achieved through several methods, each with its own set of advantages and use cases. Below are five ways to mask data:
1. Substitution
This method involves replacing sensitive data with fictional but realistic data. For example, names and addresses might be replaced with fake ones that still look like real data. This method is commonly used in scenarios where the format and structure of the data are important but the actual data values are not.
2. Encryption
Encryption is a powerful method of data masking that involves converting data into a code that can only be deciphered with the appropriate key. While encryption can be considered a form of data masking, it’s more about protecting the data rather than masking it for use in a different context. However, for the purpose of this discussion, encryption can indeed serve as a means to protect sensitive information, making it inaccessible to unauthorized parties.
3. Nulling or Deletion
In some cases, the simplest form of data masking is to null out or delete sensitive fields altogether. This method is effective when the sensitive data is not necessary for the intended use of the dataset. For example, if a database is being used for application testing, sensitive fields like credit card numbers might be nullified to prevent any potential breach.
4. Hashing
Hashing involves transforming data into a fixed-length string of characters, known as a hash value or digest. This method is one-way, meaning it’s not possible to retrieve the original data from the hash value, making it a secure way to mask data. However, hashing is typically used for data integrity and authentication purposes rather than for creating usable masked data.
5. Scrambling
Scrambling involves rearranging the characters within a data field. For example, a date of birth might be scrambled from “1990-02-12” to “2190-02-12” or some other variation that still resembles a date but is no longer accurate. This method can be used for fields where the format needs to be preserved but the actual value does not need to be accurate.
| Data Masking Method | Description | Use Cases |
|---|---|---|
| Substitution | Replacing sensitive data with fictional but realistic data. | Development, testing, and analysis environments. |
| Encryption | Converting data into a code that can only be deciphered with the appropriate key. | Data protection, secure data transmission. |
| Nulling or Deletion | Testing environments where sensitive data is not required. | |
| Hashing | Transforming data into a fixed-length string of characters. | Data integrity, authentication, and security. |
| Scrambling | Rearranging the characters within a data field. | Preserving data format while masking actual values. |
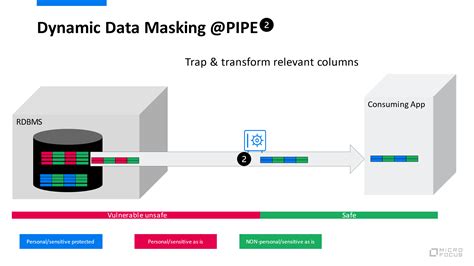
Implementing Data Masking
Implementing data masking requires careful planning and execution. Organizations should first identify what data needs to be masked, based on regulatory requirements, business needs, and risk assessments. Then, they should select the appropriate masking techniques for each type of data, considering factors like data format, data usage, and the level of protection required. Automation tools can significantly streamline the data masking process, especially in complex and large-scale data environments.
Challenges and Considerations
While data masking is a powerful tool for protecting sensitive information, it also presents several challenges and considerations. These include ensuring that masked data remains realistic and useful for its intended purposes, managing the complexity of data masking across different data sources and systems, and balancing data protection with data accessibility and usability. Furthermore, data masking must comply with various data protection regulations, such as GDPR, HIPAA, and CCPA, which mandate specific standards for data privacy and security.
What is data masking, and why is it important?
+Data masking is a data protection technique used to conceal sensitive information, replacing it with fictional but realistic data. It's crucial for compliance with data protection regulations, securing sensitive information, and enabling the safe use of data in non-production environments.
How does dynamic data masking work?
+Dynamic data masking works by hiding data in real-time, without altering the original data. It's based on policies that define what data should be masked and under what conditions, allowing for flexible and role-based access control to sensitive data.
What are the main challenges in implementing data masking?
+The main challenges include ensuring masked data remains realistic and useful, managing complexity across different data sources, balancing protection with accessibility, and complying with data protection regulations. Automation and careful planning can help mitigate these challenges.
In conclusion, data masking is a critical component of any data protection strategy, allowing organizations to safeguard sensitive information while still utilizing the data for various purposes. By understanding the different methods of data masking and carefully selecting the right techniques for specific needs, organizations can ensure compliance with data protection regulations, protect against data breaches, and maintain the integrity and usability of their data assets.