When working with event JSON, it's essential to understand the intricacies of this data format to effectively manage and analyze event-driven data. JSON, or JavaScript Object Notation, is a lightweight data interchange format that is easy to read and write, making it a popular choice for exchanging data between web servers, web applications, and mobile apps. In the context of events, JSON is used to represent event data in a structured and organized manner. Here are 5 tips for working with event JSON:
Understanding Event JSON Structure

An event JSON typically consists of a series of key-value pairs, where each key represents a specific attribute of the event, and the value is the corresponding data. For example, an event JSON for a user login event might include keys such as “eventName”, “eventType”, “timestamp”, “userId”, and “userAgent”. Understanding the structure of event JSON is crucial for effective data analysis and processing. The structure of an event JSON can vary depending on the application or system generating the event data, but it usually follows a standard format that includes essential information about the event.
Standardizing Event JSON Format
Standardizing the event JSON format is vital for ensuring consistency and facilitating data exchange between different systems. A standardized format enables easier integration with analytics tools, data warehouses, and other systems that consume event data. It’s also important to consider using established schemas or formats, such as JSON Schema, to define the structure and constraints of the event JSON. This helps in validating the data and ensuring that it conforms to the expected format. By standardizing the event JSON format, organizations can simplify their data processing pipelines and improve the overall quality of their event data.
| Event Attribute | Description |
|---|---|
| eventName | The name of the event, e.g., "userLogin" |
| eventType | The type of event, e.g., "authentication" |
| timestamp | The timestamp when the event occurred, e.g., "2023-03-01T12:00:00.000Z" |
| userId | The ID of the user who triggered the event, e.g., "12345" |
| userAgent | The user agent string of the device that triggered the event, e.g., "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3" |
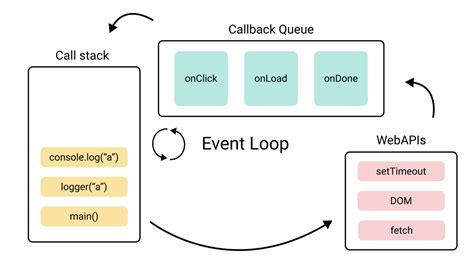
Handling Event JSON Data
Handling event JSON data requires careful consideration of data processing, storage, and analysis. One of the key challenges is dealing with large volumes of event data, which can be addressed by using distributed processing systems like Apache Kafka or Amazon Kinesis. Additionally, using data compression techniques, such as GZip or Snappy, can help reduce the storage requirements for event data. When analyzing event data, it’s essential to use analytics tools that support JSON data formats, such as Elasticsearch or Apache Spark. These tools provide efficient data processing and querying capabilities, enabling organizations to extract valuable insights from their event data.
Security Considerations for Event JSON
Security is a critical aspect of event JSON data, as it often contains sensitive information about users, systems, and applications. To ensure the confidentiality, integrity, and authenticity of event data, organizations should implement robust security measures, such as encryption, access controls, and authentication. Encryption can be applied at various levels, including data at rest and data in transit. Access controls can be implemented using techniques like role-based access control (RBAC) or attribute-based access control (ABAC). Authentication mechanisms, such as JSON Web Tokens (JWT) or OAuth, can be used to verify the identity of users and systems accessing event data.
Key Points
- Understand the structure and format of event JSON data
- Standardize the event JSON format for consistency and interoperability
- Use established schemas or formats, such as JSON Schema, to define the structure and constraints of event JSON
- Implement robust security measures, including encryption, access controls, and authentication, to protect sensitive event data
- Use analytics tools that support JSON data formats to extract valuable insights from event data
In conclusion, working with event JSON requires a deep understanding of its structure, format, and security considerations. By standardizing the event JSON format, implementing robust security measures, and using analytics tools that support JSON data formats, organizations can unlock the full potential of their event data and gain valuable insights into user behavior, system performance, and application usage.
What is event JSON, and how is it used?
+Event JSON is a data format used to represent event data in a structured and organized manner. It is commonly used in event-driven systems, such as web applications, mobile apps, and IoT devices, to exchange data between systems and analyze user behavior.
How do I standardize the event JSON format?
+To standardize the event JSON format, use established schemas or formats, such as JSON Schema, to define the structure and constraints of the event JSON. This helps ensure consistency and facilitates data exchange between different systems.
What security measures should I implement to protect event JSON data?
+To protect event JSON data, implement robust security measures, including encryption, access controls, and authentication. Use techniques like role-based access control (RBAC) or attribute-based access control (ABAC) to control access to sensitive event data.
