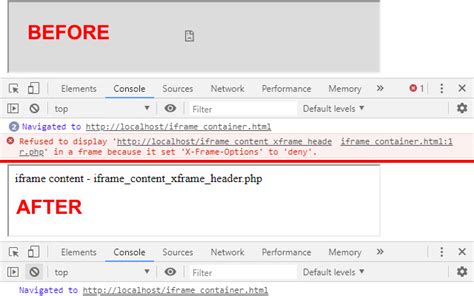
The topic of X-Frame-Options and security risks associated with ignoring these headers is a critical aspect of web application security. X-Frame-Options is a security feature that allows web developers to prevent their websites from being framed by other sites, thereby reducing the risk of clickjacking attacks. Ignoring X-Frame-Options security risks can lead to severe consequences, including compromising user data and enabling malicious activities.
X-Frame-Options Header and Its Importance

The X-Frame-Options header is a directive that instructs browsers on how to handle framing of a webpage. It can have one of three values: DENY, SAMEORIGIN, or ALLOW-FROM. The DENY value prevents any site from framing the webpage, while SAMEORIGIN allows framing only from the same origin. The ALLOW-FROM value specifies which domains are allowed to frame the webpage. Ignoring the implementation of X-Frame-Options or incorrectly configuring it can expose a website to significant security risks.
Understanding Clickjacking Attacks
Clickjacking is a type of attack where an attacker embeds a malicious webpage within an iframe on a legitimate website. When a user interacts with the iframe, they unknowingly perform actions on the malicious webpage, potentially leading to the theft of sensitive information or execution of unauthorized actions. X-Frame-Options is specifically designed to mitigate this type of attack by controlling whether a webpage can be framed and by whom.
| Header Value | Description |
|---|---|
| DENY | Prevents any site from framing the webpage. |
| SAMEORIGIN | Allows framing only from the same origin. |
| ALLOW-FROM | Specifies which domains are allowed to frame the webpage. |
Key Points
- Ignoring X-Frame-Options security risks can lead to clickjacking attacks, compromising user data and enabling malicious activities.
- The X-Frame-Options header should be correctly implemented to prevent unauthorized framing of webpages.
- Web developers must understand the different values of X-Frame-Options (DENY, SAMEORIGIN, ALLOW-FROM) and their implications on web security.
- Configuring X-Frame-Options is a critical step in securing web applications against clickjacking and other related attacks.
- Regular security audits should include checks for the proper implementation of X-Frame-Options to ensure ongoing web application security.
Consequences of Ignoring X-Frame-Options Security Risks

Ignoring the security risks associated with X-Frame-Options can have severe consequences for both web application owners and their users. These consequences include but are not limited to:
1. Clickjacking Attacks: As mentioned, ignoring X-Frame-Options can make a website vulnerable to clickjacking attacks, where attackers can trick users into performing unintended actions.
2. Data Theft: Through clickjacking and other malicious activities enabled by the lack of proper X-Frame-Options configuration, attackers can steal sensitive user data, including login credentials, financial information, and personal data.
3. Reputation Damage: A security breach resulting from ignoring X-Frame-Options security risks can lead to significant damage to a company's reputation. Users may lose trust in the company, leading to a decline in business.
4. Financial Losses: Beyond the direct financial losses from stolen data or malicious transactions, companies may also face financial penalties and legal actions following a security breach.
Mitigating Security Risks with X-Frame-Options
To mitigate the security risks associated with X-Frame-Options, web developers should:
- Implement the X-Frame-Options header with an appropriate value (DENY, SAMEORIGIN, or ALLOW-FROM) based on the specific requirements of their web application.
- Regularly audit their web application's security configuration to ensure that X-Frame-Options is correctly implemented and up-to-date.
- Stay informed about the latest web security best practices and updates to the X-Frame-Options standard.
What is the primary purpose of the X-Frame-Options header?
+The primary purpose of the X-Frame-Options header is to prevent clickjacking attacks by controlling whether a webpage can be framed by another webpage and specifying the domains that are allowed to frame it.
How can ignoring X-Frame-Options security risks affect web application security?
+Ignoring X-Frame-Options security risks can expose a web application to clickjacking attacks, potentially leading to data theft, reputation damage, and financial losses. It compromises the security of user interactions and data, making the web application vulnerable to malicious activities.
What are the recommended practices for implementing X-Frame-Options?
+Recommended practices include implementing the X-Frame-Options header with a suitable value (DENY, SAMEORIGIN, or ALLOW-FROM) based on the web application's specific needs, regularly auditing the security configuration, and staying updated with the latest web security best practices and standards.
In conclusion, ignoring X-Frame-Options security risks can have severe consequences for web application security, including enabling clickjacking attacks and compromising user data. It is essential for web developers to understand the importance of X-Frame-Options, implement it correctly, and regularly review their web application’s security configuration to prevent such risks. By taking these steps, developers can significantly enhance the security of their web applications and protect user data from malicious activities.