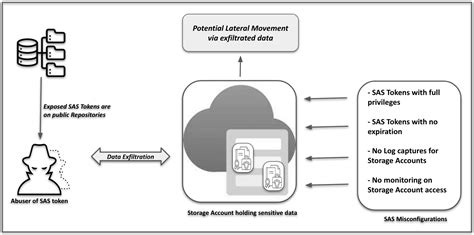
Token misconfiguration is a common issue that can arise in various systems, including authentication, authorization, and even in the context of blockchain and cryptocurrency. It refers to the incorrect setup or management of tokens, which are used to represent rights, permissions, or values within a system. When tokens are misconfigured, it can lead to security vulnerabilities, system failures, or inefficiencies. In this article, we will explore five ways to fix token misconfiguration, focusing on practical solutions and expert insights.
Understanding Token Misconfiguration

Before diving into the solutions, it’s essential to understand the nature of token misconfiguration. Tokens can be used in different contexts, such as JSON Web Tokens (JWT) for authentication, tokens in smart contracts for blockchain interactions, or even tokens in networking for access control. Misconfiguration can occur due to incorrect token issuance, improper token validation, or insufficient token management. This can lead to unauthorized access, data breaches, or system downtime.
Identifying Token Misconfiguration
Identifying token misconfiguration requires a thorough analysis of the system’s token management processes. This includes reviewing token issuance policies, validation mechanisms, and token storage practices. It’s also crucial to monitor system logs for any signs of token-related issues, such as frequent token validation errors or unexpected token expiration. By identifying the root cause of the misconfiguration, you can apply targeted solutions to fix the issue.
| Token Misconfiguration Symptom | Potential Cause |
|---|---|
| Frequent Token Validation Errors | Incorrect Token Issuance or Validation Mechanism |
| Unexpected Token Expiration | Insufficient Token Renewal or Revocation Process |
| Unauthorized Access | Insecure Token Storage or Transmission |
5 Ways to Fix Token Misconfiguration
Fixing token misconfiguration requires a systematic approach that involves understanding the root cause, applying corrective measures, and ensuring preventive mechanisms are in place. Here are five ways to address token misconfiguration:
1. Review and Update Token Issuance Policies
The first step in fixing token misconfiguration is to review and update token issuance policies. This involves ensuring that tokens are issued correctly, with the appropriate permissions, and for the intended duration. It’s crucial to define clear policies for token issuance, validation, and revocation to prevent misconfiguration.
2. Implement Robust Token Validation Mechanisms
Implementing robust token validation mechanisms is critical to preventing token misconfiguration. This includes using secure algorithms for token signing and validation, ensuring tokens are properly formatted, and verifying token contents against expected values. Regularly updating and patching validation mechanisms can also help protect against known vulnerabilities.
3. Ensure Secure Token Storage and Transmission
Secure token storage and transmission are vital to preventing unauthorized access and token misconfiguration. This involves using secure storage solutions, such as encrypted databases or secure token vaults, and transmitting tokens over secure channels, like HTTPS. Implementing access controls and auditing token access can also help detect and prevent token misconfiguration.
4. Develop and Implement Token Renewal and Revocation Processes
Developing and implementing token renewal and revocation processes can help manage token lifecycles and prevent misconfiguration. This involves establishing procedures for renewing tokens before they expire, revoking tokens when they are no longer needed, and ensuring that revoked tokens are properly handled to prevent reuse.
5. Monitor and Analyze Token-Related Activities
Finally, monitoring and analyzing token-related activities can help identify and address token misconfiguration issues before they become critical. This involves tracking token issuance, validation, and revocation, as well as monitoring system logs for signs of token-related errors or security incidents. Regular analysis of token-related data can provide insights into potential misconfiguration issues, allowing for proactive measures to prevent and fix problems.
Key Points
- Understanding the root cause of token misconfiguration is crucial for applying targeted solutions.
- Reviewing and updating token issuance policies can help prevent misconfiguration.
- Implementing robust token validation mechanisms and secure token storage and transmission practices are essential for token security.
- Developing and implementing token renewal and revocation processes can help manage token lifecycles.
- Monitoring and analyzing token-related activities can provide insights into potential misconfiguration issues.
In conclusion, fixing token misconfiguration requires a comprehensive approach that involves understanding the root cause, applying corrective measures, and ensuring preventive mechanisms are in place. By following these five ways to fix token misconfiguration, you can enhance the security and efficiency of your systems and prevent potential issues related to token management.
What is token misconfiguration, and how does it occur?
+Token misconfiguration refers to the incorrect setup or management of tokens, which can occur due to various reasons such as incorrect token issuance, improper token validation, or insufficient token management.
How can I identify token misconfiguration in my system?
+Identifying token misconfiguration requires a thorough analysis of the system’s token management processes, including reviewing token issuance policies, validation mechanisms, and token storage practices, as well as monitoring system logs for signs of token-related issues.
What are the consequences of token misconfiguration?
+The consequences of token misconfiguration can include security vulnerabilities, system failures, or inefficiencies, leading to unauthorized access, data breaches, or system downtime.