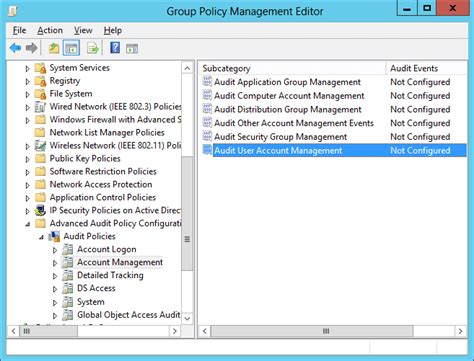
Auditing user accounts is a critical aspect of maintaining the security and integrity of any computer system or network. It involves regularly reviewing and analyzing user account activity to ensure that all accounts are legitimate, up-to-date, and compliant with organizational policies. In this article, we will discuss 5 tips for auditing user accounts, highlighting the importance of this process and providing practical guidance for IT professionals and system administrators.
Key Points
- Regularly review user account activity to detect and prevent unauthorized access
- Implement a least privilege access model to minimize potential security risks
- Use automated tools to streamline the auditing process and improve efficiency
- Establish clear policies and procedures for account creation, modification, and deletion
- Continuously monitor and analyze audit logs to identify potential security threats
Tip 1: Regularly Review User Account Activity
Regularly reviewing user account activity is essential to detect and prevent unauthorized access to sensitive data and systems. This involves analyzing login attempts, file access, and other system activities to identify potential security threats. By regularly reviewing user account activity, organizations can quickly identify and respond to security incidents, minimizing the risk of data breaches and other security threats.
Using Audit Logs to Identify Security Threats
Audit logs provide a detailed record of all system activities, including user account activity. By analyzing these logs, organizations can identify potential security threats, such as unauthorized login attempts or suspicious file access. For example, a study by the Ponemon Institute found that 60% of organizations experienced a data breach due to unauthorized access, highlighting the importance of regularly reviewing user account activity.
| Audit Log Category | Description |
|---|---|
| Login Attempts | Records of all login attempts, including successful and unsuccessful logins |
| File Access | Records of all file access, including reads, writes, and deletes |
| System Changes | Records of all system changes, including software installations and configuration changes |
Tip 2: Implement a Least Privilege Access Model
Implementing a least privilege access model is critical to minimizing potential security risks. This involves granting users only the privileges and access necessary to perform their job functions, reducing the risk of unauthorized access to sensitive data and systems. By implementing a least privilege access model, organizations can reduce the attack surface and prevent lateral movement in the event of a security breach.
Benefits of Least Privilege Access
The benefits of least privilege access include reduced security risks, improved compliance, and increased efficiency. By granting users only the privileges and access necessary to perform their job functions, organizations can reduce the risk of unauthorized access and improve compliance with regulatory requirements. For example, a study by Forrester found that organizations that implemented a least privilege access model experienced a 50% reduction in security incidents.
Tip 3: Use Automated Tools to Streamline the Auditing Process
Using automated tools to streamline the auditing process can improve efficiency and reduce the risk of human error. Automated tools can analyze audit logs, identify potential security threats, and provide real-time alerts and notifications. By using automated tools, organizations can improve the effectiveness of their auditing processes and reduce the risk of security breaches.
Benefits of Automated Auditing Tools
The benefits of automated auditing tools include improved efficiency, reduced risk of human error, and real-time alerts and notifications. Automated tools can analyze large volumes of audit log data, identifying potential security threats and providing real-time alerts and notifications. For example, a study by Gartner found that organizations that used automated auditing tools experienced a 30% reduction in security incidents.
Tip 4: Establish Clear Policies and Procedures for Account Creation, Modification, and Deletion
Establishing clear policies and procedures for account creation, modification, and deletion is critical to ensuring the security and integrity of user accounts. This involves defining the procedures for creating, modifying, and deleting user accounts, as well as the roles and responsibilities of system administrators and other stakeholders. By establishing clear policies and procedures, organizations can ensure that user accounts are properly managed and that security risks are minimized.
Importance of Clear Policies and Procedures
Clear policies and procedures are essential to ensuring the security and integrity of user accounts. By defining the procedures for creating, modifying, and deleting user accounts, organizations can ensure that user accounts are properly managed and that security risks are minimized. For example, a study by the SANS Institute found that organizations with clear policies and procedures experienced a 25% reduction in security incidents.
Tip 5: Continuously Monitor and Analyze Audit Logs to Identify Potential Security Threats
Continuously monitoring and analyzing audit logs is critical to identifying potential security threats and preventing security breaches. This involves regularly reviewing audit logs to identify suspicious activity, such as unauthorized login attempts or suspicious file access. By continuously monitoring and analyzing audit logs, organizations can quickly identify and respond to security incidents, minimizing the risk of data breaches and other security threats.
What is the importance of auditing user accounts?
+Auditing user accounts is critical to maintaining the security and integrity of any computer system or network. It involves regularly reviewing and analyzing user account activity to ensure that all accounts are legitimate, up-to-date, and compliant with organizational policies.
How can organizations implement a least privilege access model?
+Organizations can implement a least privilege access model by granting users only the privileges and access necessary to perform their job functions. This involves regularly reviewing and updating user accounts to ensure that users have only the privileges and access necessary to perform their job functions.
What are the benefits of using automated auditing tools?
+The benefits of using automated auditing tools include improved efficiency, reduced risk of human error, and real-time alerts and notifications. Automated tools can analyze large volumes of audit log data, identifying potential security threats and providing real-time alerts and notifications.